Don’t make your SOC blind to Active Directory attacks: 5 surprising behaviors of Windows audit policy
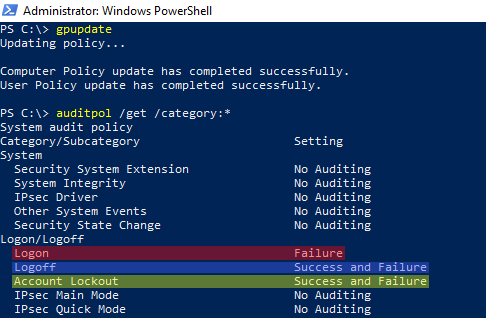
Windows offers built-in audit policy settings to configure which events should be logged. But when testing those options, we noticed surprising behaviors that can lead to missed events. When you configure your Active Directory domain controllers to log security events to send to your SIEM and raise alerts, you absolutely do not want any regression which would ultimately blind your SOC! In this article we will share technical tips to prevent those unexpected issues.
➡️ Discover this article on Tenable’s TechBlog: Don’t make your SOC blind to Active Directory attacks: 5 surprising behaviors of Windows audit policy
Read more...