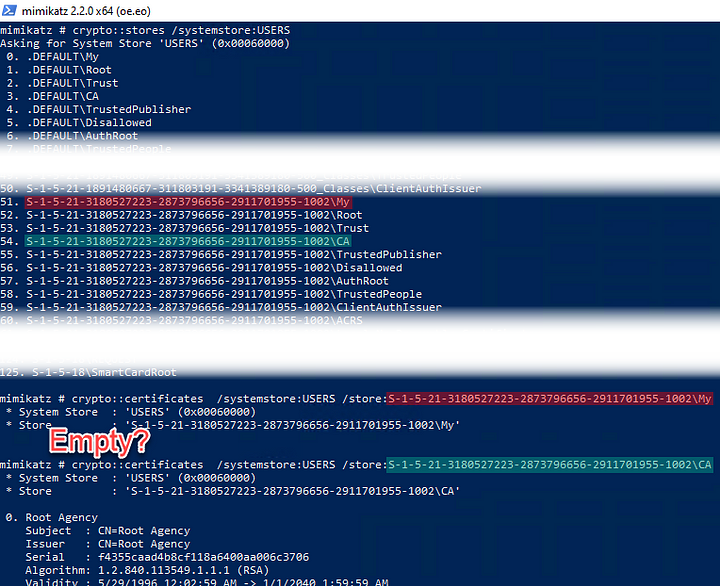
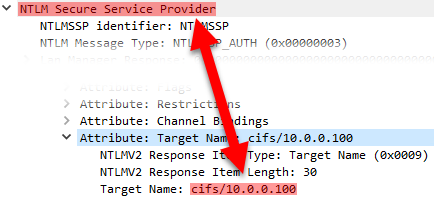
Active Directory Trust Misclassification: Why Old Trusts Look Like Insecure External Trusts
Active Directory anomaly 😯 intra-forest trusts created under Windows 2000 lack a key identifying flag, even after domain and forest upgrades. Learn how to find this legacy behavior persisting to this day, and use crossRef objects to correctly distinguish these trust types 👌
➡️ Find this article on Tenable’s blog: Active Directory Trust Misclassification: Why Old Trusts Look Like Insecure External Trusts
Read more...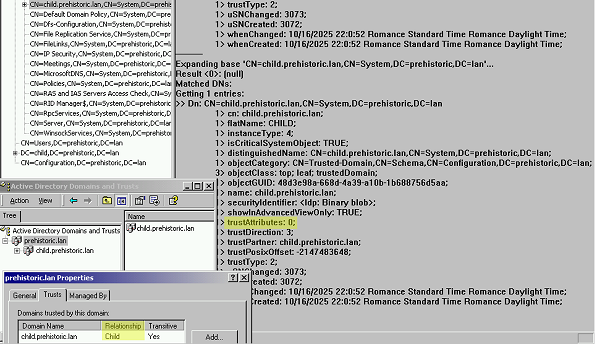
![[french] Podcast IFTTD - 308 - Sécuriser l'AD feature image](/img/logo_ifttd.png)
![[french] Conférence Identity Days 2023 feature image](/img/identity-days.png)