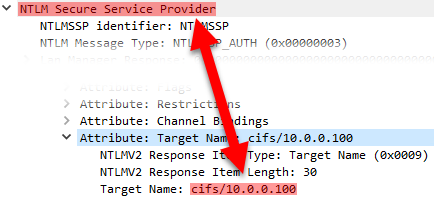
I investigated a situation where an SMB client could not connect to an SMB server. The SMB server returned an “Access Denied” during the NTLM authentication, even though the credentials were correct, etc. The only unusual thing is that the SMB server was accessed through a NAT mapping! Which made me think that this setup was in fact similar to an NTLM relay (aka SMB relay) attack. 💡 And indeed, the server had the “Microsoft network server: Server SPN target name validation level” policy (i.e. SmbServerNameHardeningLevel registry key) enabled which blocked this scenario!
😉 This situation could also occur in your regular SMB environments, so follow along to see how to troubleshoot this, how it is configured, how it works and what we suggest to do in this case.
➡️ Find this article on Tenable’s TechBlog: SMB “Access is denied” caused by anti-NTLM relay protection