
You may have deployed Splunk Universal Forwarders on your systems to forward to your SIEM, but what if they are not properly secured and could be hijacked? Attackers could leverage them to remotely execute code (RCE)!
I share two new tools to demonstrate this technique.
Background - SplunkWhisperer 🔗
I relied on the original work of @airman604 who clearly documented the issue one year ago (February 2018): Splunk Universal Forwarder Hijacking. He also shared the splunk_whisperer tool to demonstrate the issue.
His original tool is based on Python and works locally and remotely. It temporarily changes the UF (Universal Forwarder) settings to make it use an attacker controlled server as the deployment server, thus allowing the attacker to deploy a new malicious application. The configuration is then reverted back to normal.
New work - SplunkWhisperer2 🔗
I wanted a tool that was less invasive (does not change the configuration), and that could work fine standalone and local-only on Windows computers for Local Privilege Escalation.
Actually, I created two tools with the same objective. One is based on Python and the other on C#. Both can be compiled and run locally on Windows. I decided to call it “SplunkWhisperer2”.
- You have a local shell on a Windows computer running Splunk UF?
- If .NET 4.5, or later, is available (or you don’t know), use “SharpSplunkWhisperer2”
- Otherwise, use “PySplunkWhisperer2_local”
- You can contact remotely the Splunk UF API (HTTPS port 8089 by default) and you have the credentials? Note: the default credentials are admin/changeme but they do not work remotely by default
“PySplunkWhisperer2” works fine on Linux targets too (adapt the payload file name and content accordingly).
Note also that “SharpSplunkWhisperer2” relies on the Splunk SDK for C# library, whereas “PySplunkWhisperer2” directly calls the Splunk REST API.
Screenshots 🔗
If you want to test, you can download Splunk UF for free. You do not need a full Splunk deployment. I tested it successfully on Splunk UF 7.1.3.0 and 7.2.4.
-
Splunk UF now asks to setup admin credentials during the installation:
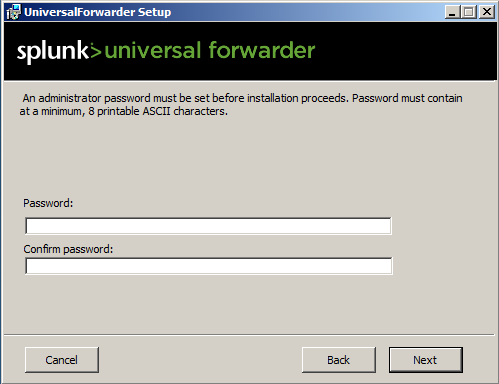
-
Splunk UF can run as SYSTEM (default, and selected for my tests) or domain user:
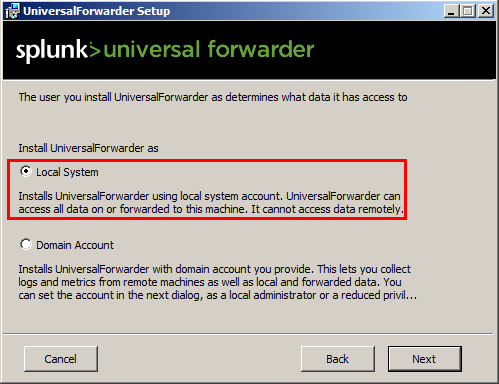
-
Obtaining a SYSTEM calc with PySplunkWhisperer2 used in local mode:
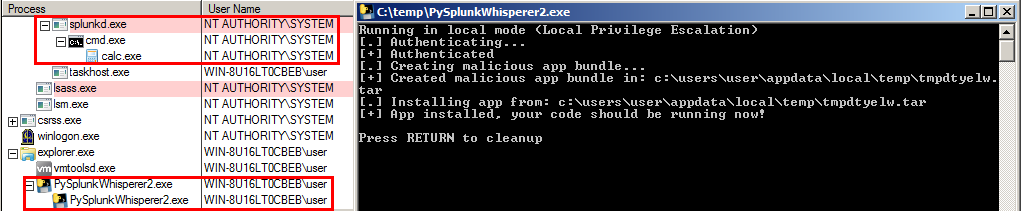
-
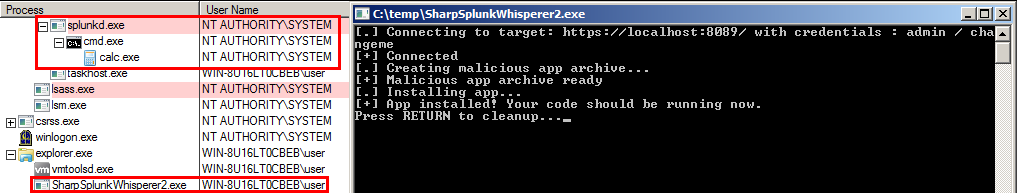
Obtaining a SYSTEM calc with SharpSplunkWhisperer2 used in local mode:
Remediations 🔗
As explained by @airman604, administrators have two options:
- Change the password. Custom techniques are possible or you can use an application such as “UF Password Changer”
You could do it manually too, for example with:"C:\Program Files\SplunkUniversalForwarder\bin\splunk.exe" edit user admin -password [FIXME] -auth admin:changeme - Disable the management port on the forwarder. Refer to his article for more details.
- The following options are also available in server.conf
# The following 'allowRemoteLogin' setting controls remote management of your splunk instance.
# - If set to 'always', all remote logins are allowed.
# - If set to 'never', only local logins to splunkd will be allowed. Note that this will still allow
# remote management through splunkweb if splunkweb is on the same server.
# - If set to 'requireSetPassword' (default behavior):
# 1. In the free license, remote login is disabled.
# 2. In the pro license, remote login is only disabled for the admin user that has not changed their default password
allowRemoteLogin=requireSetPassword
I also add that, like other services, Splunk UF should run with the lowest privileges possible. Check what privileges are required to read the relevant logs, and use an appropriate service account instead of SYSTEM.
Disclaimer 🔗
Resources provided here are shared to demonstrate risk. These can be used only against systems you own or are authorized to test, these must not be used for illegal purposes. The author cannot be held responsible for any misuse or damage from any material provided here.