
This vulnerability affects the Fortinet FortiClient program. FortiClient is a client program used to connect to SSL/IPsec VPN endpoints.
A setting, disabled by default, enables FortiClient on the logon screen to allow users to connect to a VPN profile before logon. An attacker, with physical, or remote (e.g. through TSE, VNC…), access to a machine with FortiClient and this feature enabled, can obtain SYSTEM level privileges from the lock screen. No account or prior knowledge is required.
The vulnerability lies in the confirmation dialog shown when the server certificate is not valid (e.g. default auto-signed certificate, or Man-In-The-Middle with SSL/TLS interception situation).
Exploitation 🔗
1. Install FortiClient on an Active Directory joined machine
2. Create VPN connection in FortiClient with a FortiGate endpoint using default certificate
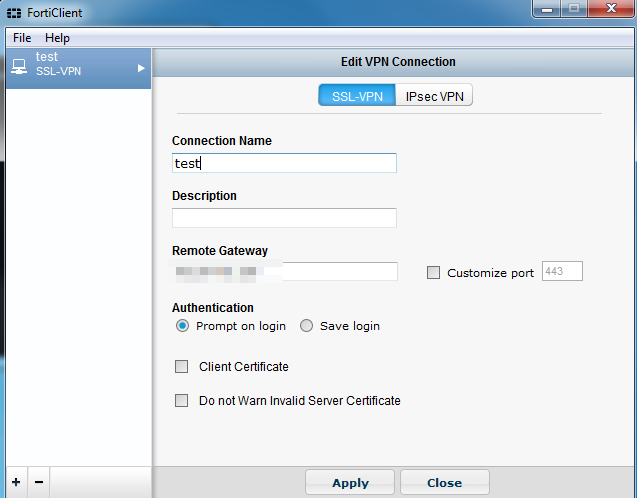
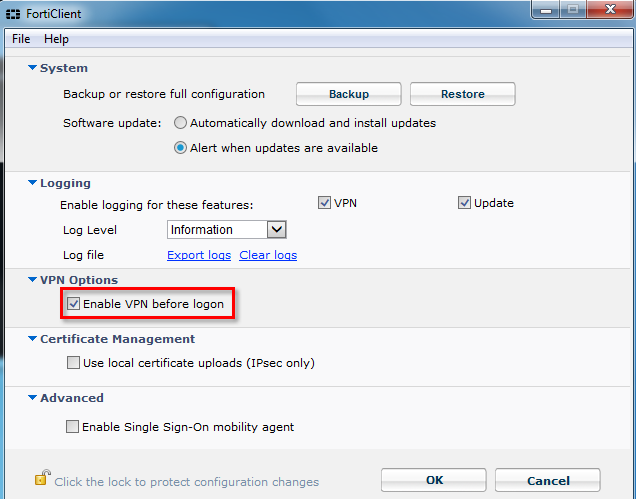
3. Enable “VPN before logon” setting in FortiClient
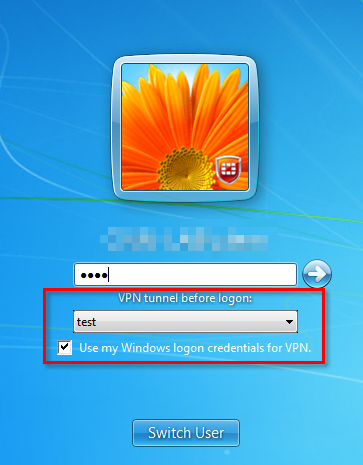
4. Log off
5. On the logon screen, select the VPN profile and type any password
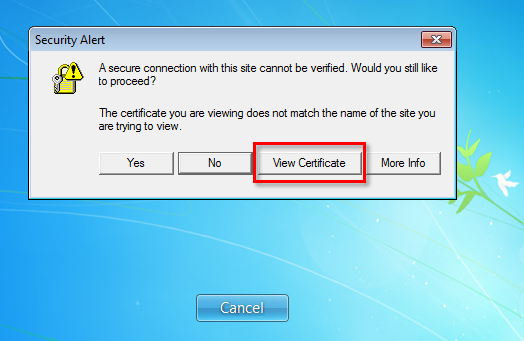
6. When connecting, the confirmation dialog will appear, click on “View certificate”
7. Go to “Details” tab then click on “Copy to file”
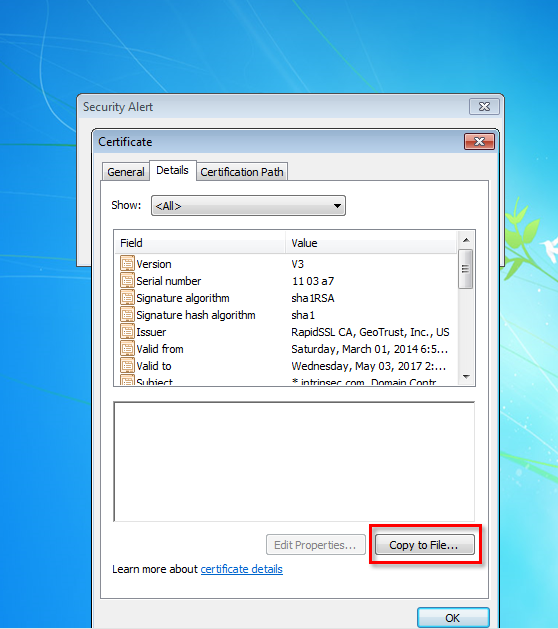
8. Click next until the screen with “Browse” button
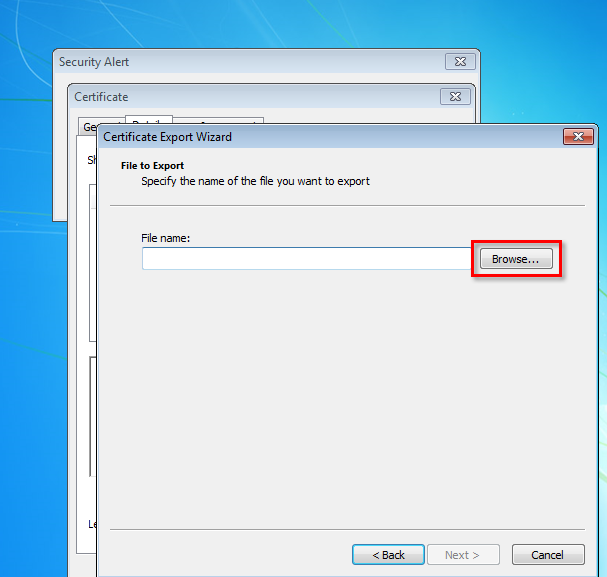
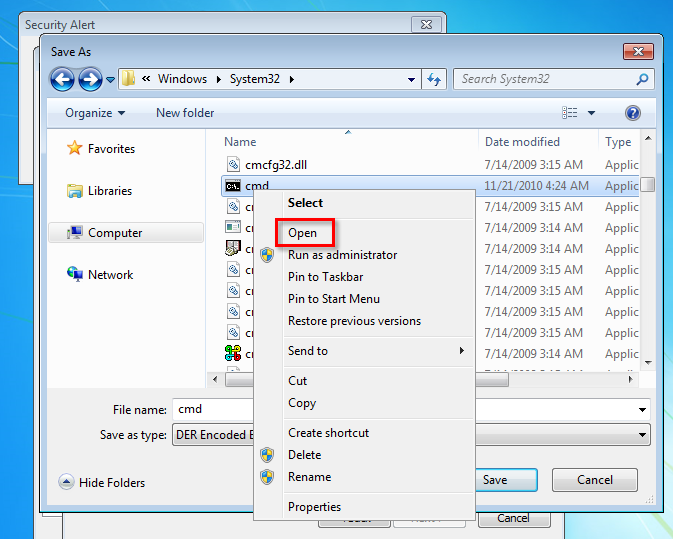
9. Browse to “C:\Windows\System32”, type a wildcard “*” in filename to show every files. Find cmd.exe, right click then click “Open”
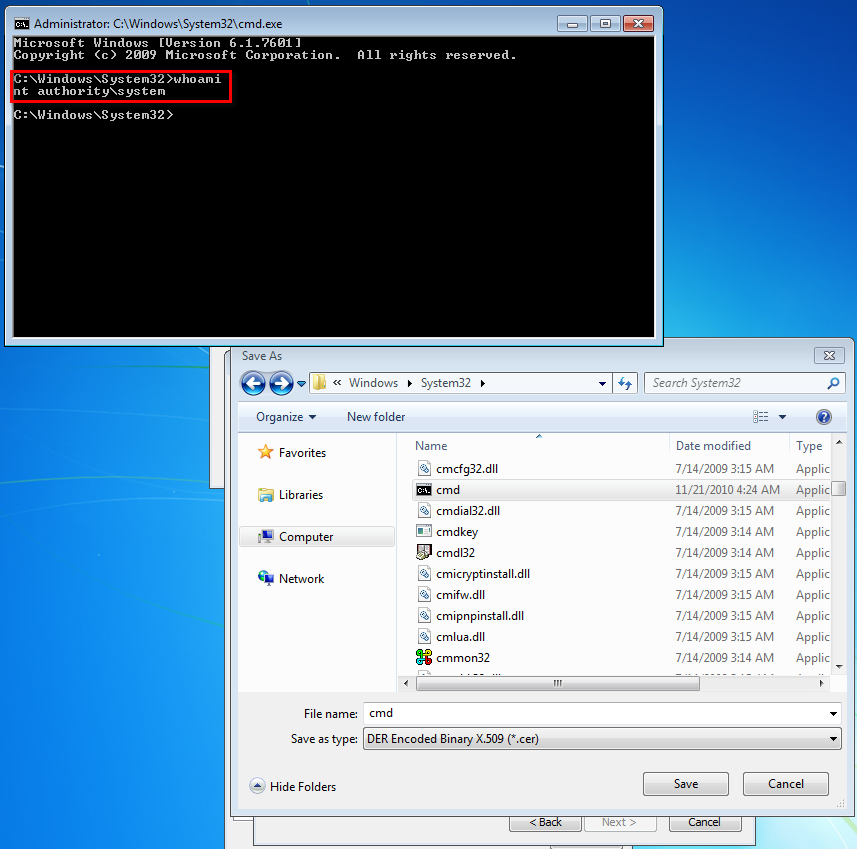
10. You get a shell with SYSTEM privileges
External references 🔗
- Fortinet PSIRT Advisory: FG-IR-17-070
- MITRE CVE: CVE-2018-15481
- NIST NVD: CVE-2018-15481
- CERT-FR: CERTFR-2017-AVI-471
- SecurityFocus: BID 102176